Cilium: Programmable Linux Networking with Dan Wendlant and Thomas Graf
Dan and Thomas join the show today to talk about why Cilium is a great choice for organizations looking to build cloud native applications
Dan and Thomas join the show today to talk about why Cilium is a great choice for organizations looking to build cloud native applications
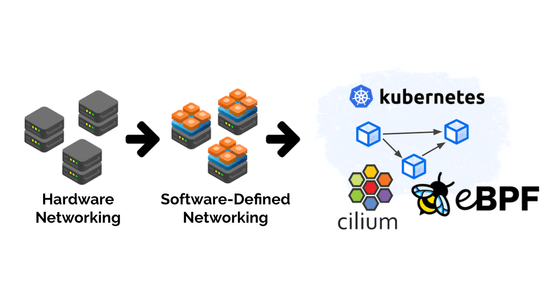
Today is an exciting day for the Cilium community: Isovalent, the company behind Cilium, is announcing its $29M Series A financing round backed by Andreessen Horowitz, Google, and Cisco. This is a perfect occasion to take a deeper look into where eBPF-based networking is coming from and to understand what the excitement is all about.
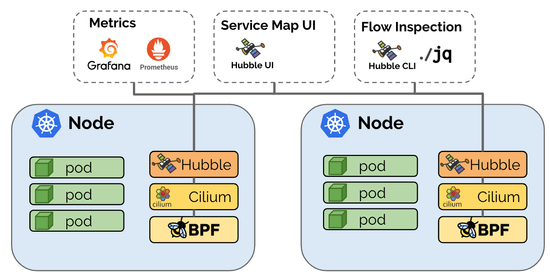
Hubble is a fully distributed networking and security observability platform for cloud native workloads. Hubble is open source software and built on top of Cilium and eBPF to enable deep visibility into the communication and behavior of services as well as the networking infrastructure in a completely transparent manner.

Thomas Graf discusses the recent 1.6 release, some of the security questions/concerns around eBPF, and the future roadmap for the project
On May 25 2019, a security relevant bug has been reported to us via the documented security disclosure channel. It was soon identified that multiple vendors are affected by this vulnerability. This lead to an embargo period which is being lifted today. The bug allows, under certain circumstances, to bypass network security policies. See below for details on the vulnerability and the mitigation.
We have covered Facebook's BPF-based load balancer with DDoS protection in a previous blog post. This post provides further details on Facebook's BPF use by covering Anant Deepak's talk at the BPF/networking microconference on Facebook's BPF-based edge firewall running in production.
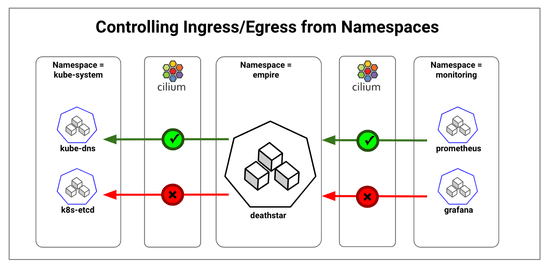
Kubernetes clusters are used by multiple tenants to run their containerized workloads. Often, the tenant workloads are mapped to namespaces and strict access control is required for inter-namespace communications. The access control could be needed for separation of concerns such as monitoring namespace vs application namespace; for compliance such as PCI vs non-PCI workloads; or to meet requirements of serving different end customers such as workloads serving Pepsi vs Coke. In this post, we will look at namespace based segmentation of traffic along with examples of allowing specific inter-namespace communications.
Istio 1.0 was released last week. From the Cilium community, we would like to congratulate all Istio contributors for this massive effort. We have been fortunate to participate in the community by contributing to Istio and by helping several users moving towards production with Istio and Cilium.
To celebrate the Cilium project hitting 1.0, we wanted to take a moment to share the broader story behind how BPF and Cilium are driving the biggest change in the past two decades of Linux networking and security, and invite you to join in on the fun. We're just getting started!
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace